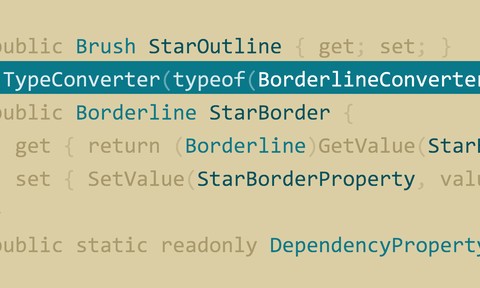
XAML is one of the primary languages used to create user interfaces for .NET and Windows 10. To develop apps with this framework, you need to be able to map relationships between .NET types and XAML objects and to work with reusable resources. This course, the third in our Microsoft XAML Fundamentals series, shows how to use type convertors and markup extensions to convert XAML properties to .NET properties, and how to create, organize, and consume XAML resources. Instructor Walt Ritscher also explains how to enable XAML styles, templates, and shared colors and brushes via resources, and load external resource files with merged dictionaries.
Learn More